Thursday, October 4, 2007
WiMax Technology
Among the main uses of WiMax comes the internet connectivity for laptops. In a radius of upto 10 km WiMax can give access rates of upto 40Mbps per channel. In India(a south asian fast developing economy), WiMax network is being setup in Chennai, a city in south of India. This technology if spreads out to the entire country can benefit the 1 billion citizens of India, especially the villages of India where still for many using internet remains a dream.
Associated Links :
Monday, October 1, 2007
CDMA or GSM
In CDMA there is no division of frequency band unlike GSM which assigns a specific frequency to each user. Each user in GSM is identified using the SIM(Subscriber Identity module) card which stores the service subscriber key used to identify the user.

On the left is shown a CDMA phone by Tata Indicom.
CDMA employs spread spectrum technology in which the energy generated in a particular bandwidth is spread in the frequency band. This frequency band is used for all the users. It provides better bandwidth for the voice and data transmission over the network and hence increases the number of people that can be connected at any given time. This means using it you will hear less of those irritating("Network is currently busy") messages. Surely CDMA provides high speed services.
But inspite of all these benefits of CDMA we cannot forget the advantage given to SIM card owners to easily change their mobile phones.
Friday, September 28, 2007
Removing the hand icon displayed below shared drives
Open regedit ( Go to start>Run and type in regedit) .
- Browse to the location HKEY_CLASSES_ROOT>Network>Sharing Handler.
- Open the default icon by double clicking it.
- In the value data textbox the default value is ntshrui.dll.
- Erase this value to leave the space blank.
- Restart your PC and see the change in the icon of your shared drives.
Thursday, September 20, 2007
Disabling Windows Error Reporting
- Open the control panel
- Double click on the System icon
- Click on the Advanced tab
- Click on the button named "Error Reporting"
- Now on the window that appears click disable error reporting as shown.
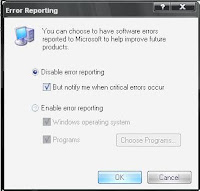
Well now you can fell free of those irritating error reporting messages and enjoy your work on the PC.
Sunday, September 16, 2007
Renaming the Recycle Bin
When you right click on the recycle bin unlike other icons, the rename option is not displayed in the pop-up menu. But this doesn't mean it can;t be changed. Well now it's time to open up regedit. For that go to the Start>run. Then type regedit. You will be presented with a screen as shown below :

Now go to the location "HKEY_CLASSES_ROOT/CLSID/{645FF040-5081-101B-9F08-00AA002F954E/ShellFolder/}" by expanding the '+' signs.
Once you reach there double click the "Attributes" icon.
Then change the value data from "40 01 00 20" to "50 01 00 20".
Now double click "CallForAttributes" icon and change the value data to 0.
Rejoice! Now you can jump back to your desktop and right click the recycle bin to see the rename option. Click it and name the recycle bin to whatever you want.
Some tweaks you can perform (Always remember to create a backup of your registry before performing any of the registry tweaks) :
Wednesday, September 12, 2007
Auto shut down of the computer for firefox download
For all you guys who work on firefox most of the time, there is a Add-on provided by firefox which allows you to turn off your computer once the list of download items finishes. It adds an icon to the status bar and the download manager, which enables you to automatically shut your computer down once the download has finished. To download this add-on click here.
Sunday, September 9, 2007
Creating a Bootable Pen Drive
But this cool way might not shine the light equally on everyone. In order to boot from a flash drive your system should be only around two years old. An alternative to this is that you upgrade your BIOS. Also the flash drive you use should be of a minimum of 256 Mb size to hold windows XP. Also a maximum size of 2GB is permissible.
So now you have the pendrive and an approprite BIOS. So get started with creating a bootable pen drive. For that you need to have a USB Disk storage format tool which is available for free. Now you can start formatting your pen drive. Then to make it bootable copy the following files on to the pen drive : Boot.ini, NTLDR, and NTDETECT from root directory of the boot drive.
Now you will be needing a software named BartPE that helps you install windows on a minimal space. After you have downloaded it follow the steps to copy the Windows files.
After you are done with all this you are having your very own flash drive ready to boot your Windows XP2.
Associated links :
Thursday, September 6, 2007
NTFS (New Technology File System)
A file system is a part of the operating system that determines how files are named, stored and organized on a volume. FAT (File allocation table ) was the standard file system developed by microsoft for the MS-DOS. This was used in all the windows till the Windows ME. Then came the NTFS (New Technology File System) which almost replaced the FAT file allocation.
The NTFS allows greater reliability, security, greater volume size etc. In NTFS all the characteristics of the file (like filename, date of creation) are stored as metadata. NTFS utilizes the power of B+ trees to index file system data. The master file table is used to store the metadata about every file present on the volume. In this system greater security is provided as we can restrict access of files to authorized users.
These features of NTFS sure does give them a reason to be chosen while opting for the type of file system for formatting.
Associated topics :
Monday, September 3, 2007
Rules for Creating a Relational DBMS
(1)Information Rule:
All information in a relational database including table names,column names are
represented explicitly by values in tables. Knowledge of only one language is necessary to
access all data such as description of the table and attribute definitions ,integrity
constraints,action to be taken when constraints are voilated,and security information.
(2)Guaranted Access Rule:
Every pieceof data in the relational database,can be accessed by using a
combination of a table name, a primary key value that identifies the row and a column
that identifies the cell.The benefit of this is that user productivity is improved
since there is no need to resort to using physical pointers addresses.Provides
data independence.
(3)Systematic treatment of Nulls Rule:
The RDBMS handles that have unknown on inapplicable values in a predefined fashion.
RDBMS distinguishes between zeros,blanks and nulls in records and handles such values in
a consistent manner that produces correct answers,comparisions and calculations.
(4)Active On-Line Catalog Based on the Relational Model.
THe description of a database and its contents are database tables and therefore
can be queries online via the data language.The DBA's productivity is improved since
changes and additionsto the catalog can be done with the same commands that are
used to access any other table.All queries and reports can be done as with other tables.
(5)Comprehensive Data Sublanguage Rule:
A RDBMS may support several languages,but atleast one of them allows the user to do all
of the following:define tables view,query and update data ,set integrity constraints,
set authorization,and define transactions.
(6)View Updating Rule:
Any view that is theoretically updatable,if changes can be made to the tables that
effect the desired changes in the view.Data consistency is ensured since changes
in the underlying tables are transmittedto the view they support.Logical data
independence reduces maintenance cost.
(7)High Level Inserts,Update and Delete:
THe RDBMS supports insertion,updation and deletion at a table level.With this the
RDBMS can improveperformance by optimizing the path to be taken to execute the action
Ease of use improved since commands act on set of records.
(8)Physical data Independence :
The execution of adhoc requests and application programs is not affected by changes
in the physical data access and storage methods.Database administrators can make
the changes to physical acccess and storage methods ,which improve performance
but do not changes in the application programs or adhoc requests.This reduces
maintenance costs.
(9)Logical data Independence:
Logical changes in tables and view such asadding/deleting columns or changing
field lenghts do not necessitate modifications in application programs or in the
format of adhoc requests.
(10)Integrity Independance:
Like table/view definitions ,integrity constraints are atored in the
on-line catalog and therefore can be changed without necessitating changes
in application programs or in the format of adhoc requests .
The following two integrity constraints must be supported.
(a)Entity Integrity:
No component of primary key is allowed to have anull value.
(b)Referential integrity:
For each distinct non-null foreign key value in a relationaldatabase,
there must exist a matching primary key from the same range of data value.
(11)Distribution Independence:
Application programs and adhoc requests are not affected by changes
in the distribution of the physical data.
(12)Nonsubversion Rule:
If the RDBMS has a language change that accesses the information
of a record at a time,this language cannot be used to by-pass the
integrity constraints.Inoreder to adhere to this rule the RDBMS must have an
active catalog that containsthe constraints must have a logical data independence.
Thursday, August 30, 2007
Minicomputers

These minicomputers behave as a stand-alone computer with a number of terminals attached to it. They were small computers ( compared to the then existing mainframe computers ). This had been achieved with the introduction of transistors and core memory technologies.
The magnetic core memory or the ferrite core memory is a kind of computer memory. It stores information in magnetic ceramic rings which can store a bit(0 or 1) of information.

These rings are arranged in a grid form as shown.
But the minicomputers still had few drawbacks like large size, expensive to buy which gave way to the invention of the microcomputers which is visible in almost every household now a days.
Saturday, August 25, 2007
Placing a seperate hibernate button on the shut down screen
Open regedit ( click on start > run. Then type in regedit), create a key as shown below, "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System\Shutdown". Then under this key create a dword value "ShowHibernateButton" and set it's value to 1 as shown "ShowHibernateButton" = dword:00000001 .
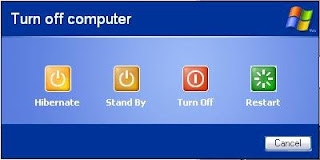
Rejoice now you can just check out your work by jumping on to the shut down screen and notice the change.
Now you will see four buttons appearing on your shut down screen. Now you will not have to bother your finger ever time you put your PC on hibernation.
Wednesday, August 22, 2007
Working Of LED's
 An LED consist of a p-n junction in which electricity is passed through it in forward biased mode as shown in the figure.
An LED consist of a p-n junction in which electricity is passed through it in forward biased mode as shown in the figure. Also a load resistance is applied to it so that the excess current does not harm the LED.
Also a load resistance is applied to it so that the excess current does not harm the LED.LED's are available in various colors to suit your need like red,blue,yellow,white etc. But the white and blue LED's are particularly costlier compared to the other colored LED's.
These LED's are tiny bulbs which can be used for various purposes like in calculators. Most significant use is the one in seven segment display, the one we see on our watches. These small bulbs are arranged in a particular pattern to create a beautiful display of a number.
There also exist the bi-colored and tri-colored LED's. So just check out the various available LED's and create something innovative out of it.
Associated Links :
Sunday, August 19, 2007
Plasma Display

A plasma display consist of two glass panels holding an inert(that is, the gases do not react) mixture of noble gases(neon and xenon). These gases are exited by electricity converting them into plasma(ionized gas). This plasma then excites the phosphors to emit light which in turn lights up the pixels.
The pixel is a point which make up the entire screen. This pixel is in turn divided into a three subpixels. In a Plasma screen each subpixel can produce millions of colors. With the combination of all such pixels we get the so-called perfect picture quality.
Associated Links :
Thursday, August 16, 2007
Technology behind LCD
 crystal gel sandwiched between two thin polarized materials. This gel is divided into small dots called as pixels. In order to darken a pixel the pixel is polarized 90 degrees to the polarizing screen. For a bright pixel the polarization is 0 degrees.
crystal gel sandwiched between two thin polarized materials. This gel is divided into small dots called as pixels. In order to darken a pixel the pixel is polarized 90 degrees to the polarizing screen. For a bright pixel the polarization is 0 degrees.Related Topics :
Cleaning an LCD TV
Free LCD TV
Monday, August 13, 2007
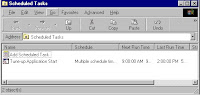
Scheduling a computer for shut down
To shut down the system at a specific time
- A wizard opens, click next. You will be presented with a list of programs you can schedule to run.
- Click on browse, locate the %SystemRoot%\System32 folder. Then find the file named Shutdown.exe and click open.
- Specify a name for the task and when do you want the task to run. Click next.
- Specify the starting date and time and click next.
- Then you will be prompted to enter the user name and password. Supply the information and click finish.
- Now you are done with the process of scheduling the computer to shut down and can go to your work without worrying about terminating the download.
Friday, August 10, 2007
Get your voice on Air ( Internet Radio )
Live365 is an internet radio provider in which members can create their own radio station and air your voice over it. You can also listen to other such members you have uploaded their voices. To get such access you have to purchase the "Broadcaster's" membership. Different packages are available to choose from depending on your requirements. In the very basic package, one can upload an MP3 file created by him, which will be relayed on the internet. Advanced members can upload the music at their home by getting handy a microphone. Get a quick access to Live365. So, if you think you play an instrument good enough or your voice is worth listening to, just start broadcasting your voice and see fame coming your way.
Tuesday, August 7, 2007
Recovering files deleted from the Recycle bin
Whenever we delete a file using the above said methods, the file is not deleted rather that file is removed from the list of files in the folder and the memory area in which the file is stored is available to windows to write something else. So, longer the period since when you have deleted the file, lesser will be the chance of it being recovered.
Defragmentation frees the space occupied by such deleted files, so if you have defragmented your hard-disk recently, you can forget the idea of recovering your file. There are many tools that help you recover your files, some are paid and some for free. So here is one such free tool named "Restoration". It helps you recover the deleted files with ease. Just give it a try.
Saturday, August 4, 2007
Wireless Monitor for your desktop
For the same you need a wireless monitor connector. Many such gadgets are available like WID101 from Teq Gear, Avocent LV3500W longview wireless extender, and many more.
A pic of the WID101 is shown below :
 This device connects the DVI port situated in your PC with the one on your monitor over an encrypted network. It can provide you a resolution of 1366*768.
This device connects the DVI port situated in your PC with the one on your monitor over an encrypted network. It can provide you a resolution of 1366*768.But in order to have this wireless connectivity you need to have a DVI(Digital Video Interface) port. This port is mostly available in the flat panel LCD monitors and some of the CRD(cathode ray display) monitors.
The DVI port looks similar to the following figure :
 Well this technology does come for a price(around $1000), but it is worth a buy if you are wretched by the amount of wires on your table.
Well this technology does come for a price(around $1000), but it is worth a buy if you are wretched by the amount of wires on your table.
Wednesday, August 1, 2007
Internet on the Go
As people have rapidly started switching over to the laptops from their traditioal desktop PC's, the need for having an internet connection that travels with you is rapidly becoming a necessity.
Thankfully many compaies are trying to take advantage of this situation, thereby simplyfying our lives. There are data cards available in the market that can be connected to the laptop or the PC.
Basically, the companies have introduced this technology using two media. First is the data card which can be inserted in the card slot embedded in your laptop. A picture of it is shown below.

- They cannot used on every laptop as not every laptop has such ports in them.
- They obviously cannot be used on a desktop PC unless you have bought an external such card reader.
The alternative to this is the USB modem which has been launched necessarily to overcome the above weaknesses. The USB modem is simply inserted in the USB port of your laptop or desktop PC. A USB modem is shown below:

But with this advantage of internet on the go you have to bear with the slow speed these tools offer. They offer a speed of around 144kbps, but one is able to get a speed of around 50kbps only. But this downside of these tools sure is overpowered by the mobility it provides to the internet connection.
These cards can be purchased for anything arount 2500-3000 bucks plus the monthly tarrifs. Providers for these technologies now a days include : Airtel, Reliance, Tata Indicom and so on. So the next time you go out on a long trip you don't have to worry about the availability of the cyber cafe.
Monday, July 16, 2007
Dynamic Link Library
DLL(Dynamic Link Library) is a file consisting of number of functions that can be called by other programs running on the computer. DLL files that help in the operation of certain devices are known as the device drivers(These are the same files that are provided in a CD with your motherboard, the so called "driver CD").
DLL files help save memory as they are not loaded into the RAM along with the program making a call to it, rather it is loaded only when an explicit call is made to it. This property of DLL's help save the precious RAM memory. A DLL file simply acts as a repository of functions which can be used by a number of applications at the same time. Also the dll file is not compiled, only a reference is provided tothe dll file to use it.
A DLL file is often given a dll extension. A DLL file differs from an exe file as it can not be run directly, it must be called from other code that is already executing. In order to use a DLL file we have to register it by providng its references in the registry. To do this goto the command line(Start>run) and type in "regsvr32 filename.dll". This will register the dll file.
In order to open up a dll file you have to use a file named ILDASM.exe. This file can be found at "C:\Program Files\Microsoft.NET\FrameworkSDK\bin" if you have the .net framework installed.
So, now don't be puzzled in seeing all those dll files on your system and try checkingout a few of them.
Sunday, April 29, 2007
Data Recovery when you need it the most
iDatacare is a nice website which helps you in performing all your data recory related issues. It handles many situations like data corruption by virus, e-mail corruption, recovery of data even if deleted from recycle bin and many more. It provides an interactive session to the users in which the user can tell the experts their problem. In response to this the experts from iDatacare take control of your computer via remote desktop connection and load a data recovery software on to your PC.
After 40 minutes of scan of your computer by the software you get your data back as it was earlier. Now the only job you are left with is to thank the guys who have helped you out.
You can also download the demo of the data recovery software and help yourself.
Thursday, April 19, 2007
Hosting a website at home
We can access any computer on the internet by its IP address (eg. http://10.25.121.2). But this way of accessing through numbers is not considered user friendly. For this purpose we make the use of DNS service to give name to the IP address. We'll use one such free DNS name provider DynDNS. It provides free static and dynamic DNS service. You can also use no-Ip as an alternative.
So now you can have a dynamic DNS account. Sometimes you might face problems in logging in to DynDNS every time your IP address changes. You can handle this by installing the DynDNS Updater software, which automatically updates your IP address in the DNS records.
To get the DNS updatig software visit DynDNS updater. On installing this software you will be asked for a hostname group, give a name to your group of hostnames.And when you reach the "Hostname Information" screen,check the box next to your hostname before clicking "Next."
Now you have your very own hostname on the Internet without troubling your wallet. For most people, the next step is to assign a static local IP address to your computer so that you have a fixed address on your home network to forward web or BitTorrent traffic to.
Tuesday, April 10, 2007
Removing the Get Genuine Notification
After this whenever you start your PC it prompts the user to buy a licenced copy. To remove this notification a small number of simple steps have to be followed :
- Go to My Computer and open the folder "C:\Windows\System32".
- Locate the file "WgaTray.exe" and rename it to "WgaTray-spyware.exe".
- Locate the file "WgaLogon.dll" and rename it to "WgaLogon-spyware.dll".
- Go to the task manager(by pressing Ctrl+Alt+Del) and end the process "Wgatray.exe" under the processes tab.
- Then just restart your computer and you will see the change.
Thursday, March 29, 2007
Having Your Presence Online
The world wide web basically began as a means to share research data, but now it has become an integral part of how we work, play and shop today. Today there are millions of sites running on the www, so why not you be the one. Here are a certain steps that will help you open up your own website.
Choosing a Free Web Host
1. Advertising: Most free web hosts impose advertising on your website. This is done to cover the costs of providing your site the free web space and associated services. Some hosts require you to place a banner on your pages, others display a window that pops up everytime a page on your site loads, while still others impose an advertising frame on your site. Whichever method is used, check that you're comfortable with the method.
2. Amount of web space: Does the host provide enough space for your needs. Most sites use less than 5MB of web space. Your needs will vary, depending on how many pictures your pages use, whether you need sound files, video clips etc.
Choosing a Good website extension (com, org, net, etc)
One common question people face is which domain name extension to use. The answer is not as straightforward as you might think. If your website or business caters to the local community, such as a free home delivery restaurant then it makes sense to get a country-specific domain. You actually benefit from having such a local domain because the people in your country know that they're dealing with a local entity. ".org" extension actually describes the non-profit nature of their organisation.
Similarly “.com” describes a commercial website, “.net “ for networking, etc.
So you can choose your websites extension as desired.
List of Free website hosts
1. http://www.freewebsites.com/ : Using this host you can get a free domain name and webspace . This host provides a domain name of the type “yourname.freewebsites.com”. It provides a webspace of 50 MB and unlimited e-mail ID.
2. http://www.freewebhosts.com/
Uploading your website
Uploading refers to the process of putting your websites content on the web server. A number of software are available on the net for uploading a website like
Smart ftp,cute ftp,etc. Also you can directly upload the file by opening the extension ftp://www.domainname.com/ in the internet explorer. This will open your home folder on the web server. Then simply drag and drop your files on this folder to upload your files.
Now you are done with the process of uploading and your website is ready to run, so just open the internet explorer, type your domain name and see your website on the world wide web.
Thursday, March 15, 2007
Switches, Hub or Routers
HUB : A Hub is a common connection point for devices in a network. They are used to form a LAN (local area network). It contains a number of ports. When a data packet arrives at one port, it is copied to the other ports so that all nodes in the LAN can see all packets.


Differences between Hub, switch and router
In a hub, a data packet is transmitted to every one of its ports The hub has no way of distinguishing to which port a packet should be sent to. A hub shares its bandwidth with each and every one of its ports. So when only one PC is working, it will have access to the maximum available bandwidth. If, however, multiple PC’s are broadcasting, then that bandwidth will be divided among all of those PC’s, which will degrade performance.
A switch, however, keeps a record of the MAC addresses of all the devices connected to it. So when a data packet is received, it knows which port to send it to. So regardless of the number of PCs transmitting, users will always have access to the maximum amount of bandwidth. Because of this a switch is considered to be a much better choice then a hub.
Routers serve a more advanced purpose. It routes packets to other networks until that packet reaches its destination. A router will typically include a 4 - 8 port Ethernet switch (or hub) and a Network Address Translator (NAT). In addition, they usually include a Dynamic Host Configuration Protocol (DHCP) server, Domain Name Service (DNS) proxy server and a hardware firewall to protect the LAN from malicious intrusion from the Internet.
All routers have a WAN Port that connects to a DSL or cable modem for broadband Internet service and the integrated switch allows users to easily create a LAN. This allows all the PCs on the LAN to have access to the Internet.
So, next time you go out to buy one of the networking media do take a look at the above discussed points.
Thursday, March 8, 2007
Maps Vs Maps
Starting with live maps :
URL : "http://maps.live.com"
It works well for India compared to others as directions for Indian states are easily located. One of the advatages was the arial view which it provided. Also business locations can be searched. Draggable maps are there which is a geat plus point. I tried for the direction from Agra to New Delhi and following was the result.
 I really liked the result.
I really liked the result.Then I checked out the google maps which are a hot stuff now a days.
URL: "http://maps.google.com"
It had almost all the features as livemaps except that it doesn't yet support direction finding for Indian states. I tried the for the direction from New York to New Jersey and this was what I got.
 Pretty much impressive.
Pretty much impressive.Then finally I tried out the msn maps.
URL : "http://mappoint.msn.com"
It was although impressive but lagged some features like draggable maps. I tried for direction between Arizona and california and this was what I got.

So from next time you go out on a trip make sure you carry a laptop and make use of the above stated direction finding maps to reach your destination with ease.